Challenge name: Brutus
Category: Web
Challenge Description:
Lets start by downloading the ip.zip file
lets extract that file you can see
i am 100% sure that its gonna have a huge lot of files so lets open terminal and find the ip
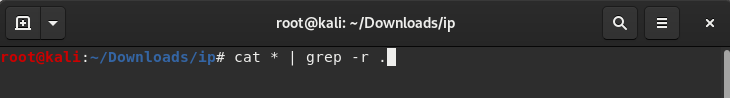
so open terminal and type in
cat * | grep -r .
the command with cat any file it sees and grep . (which is usually used in ip)
we got
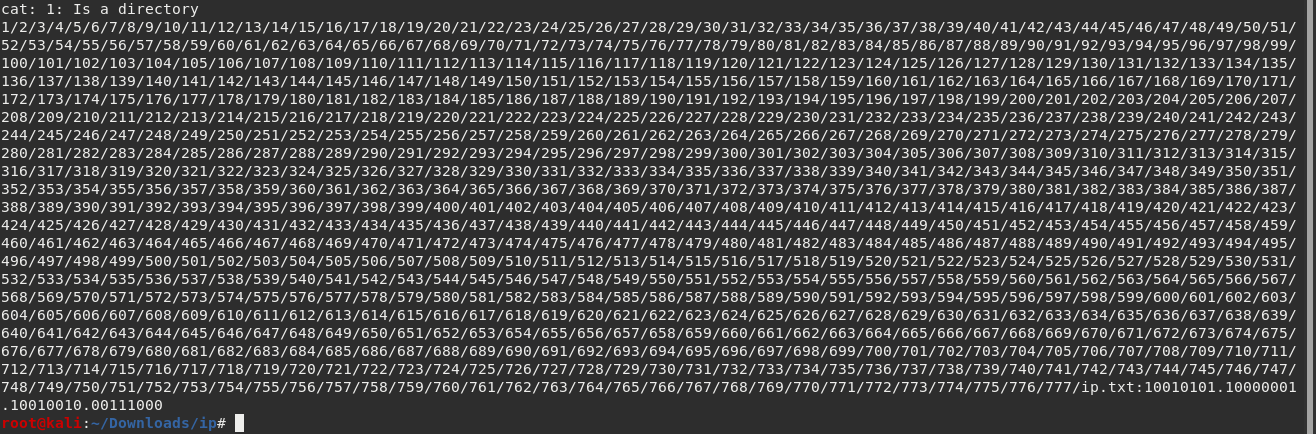
boom now since the ip is in binary lets convert it
the website i used to convert the ip,
https://www.browserling.com/tools/bin-to-ip
so lets paste the binary into the site and take our ip :)
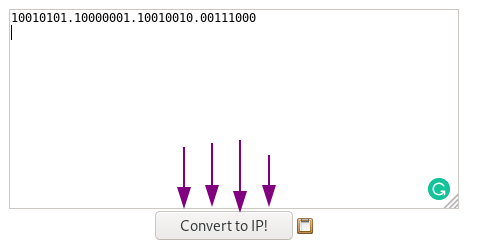
you will get your ip after converting as

149.129.146.56
lets visit the ip we will see
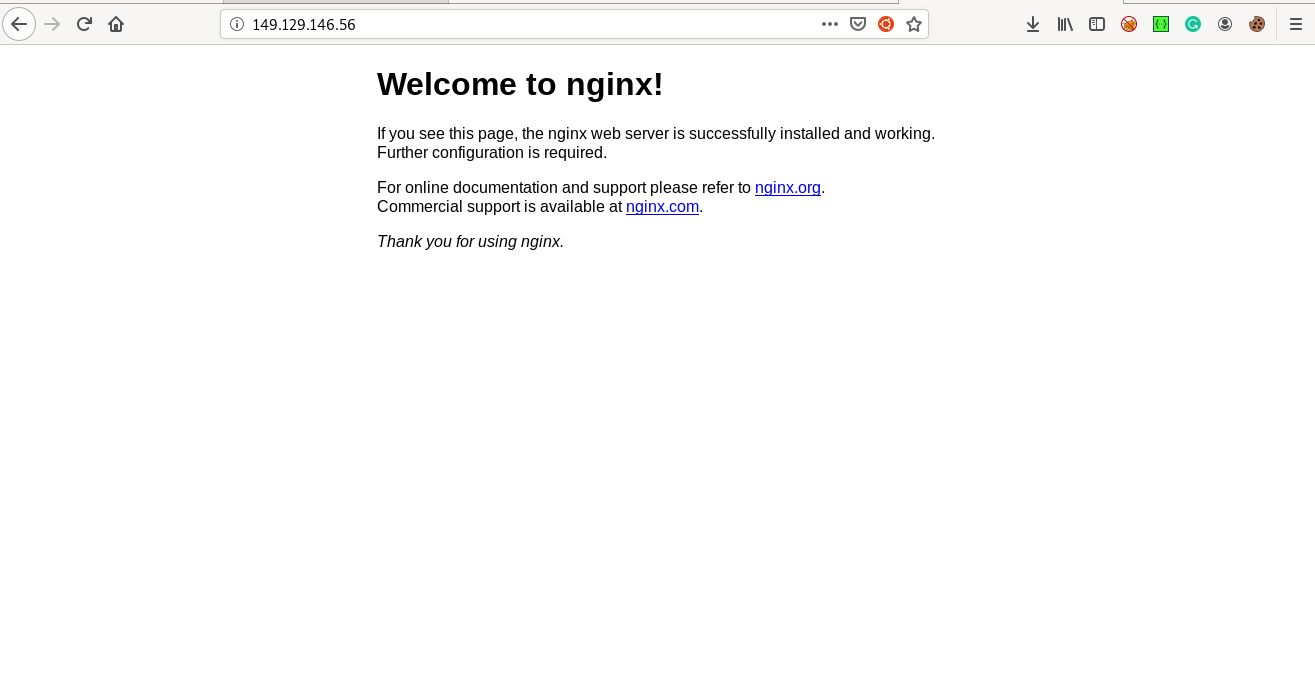
since our challenge is brutus lets visit the brutus url by
149.129.146.56/brutus
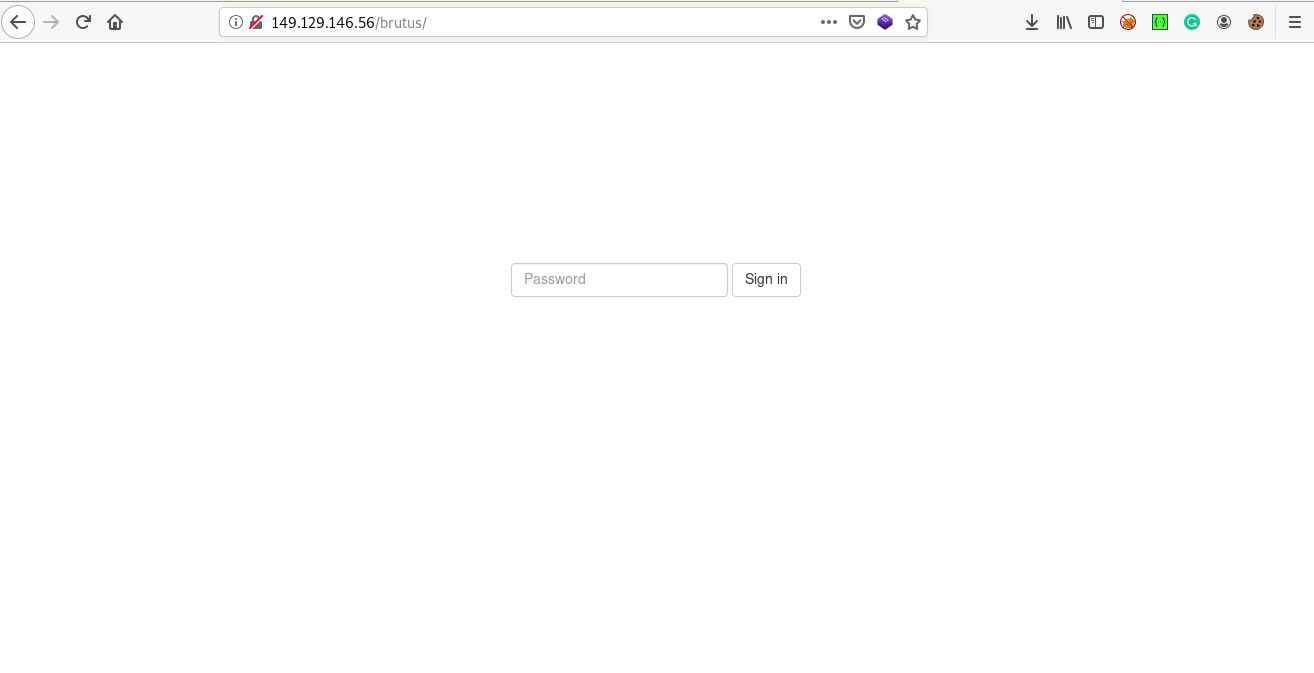
opps theres a password sign in :( remember the description of the CTF mentions something about a nepali word list lets get on the way to search for one !!!
so the person who made the wordlist is Naresh Lamgade so lets look for the wordlist
For this part i will explain how I got the nepali wordlist :)
so the person has his email nareshlamgade@gmail.com
looking with that email( google searching nareshlamgade@gmail.com)
i got an website
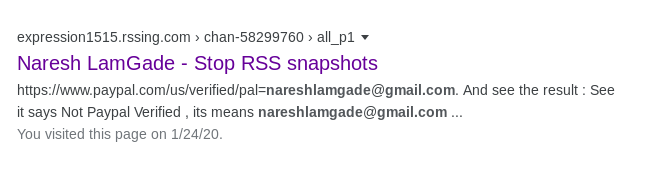
you will see website like
So lets scroll down until we see the nepali wordlist blog
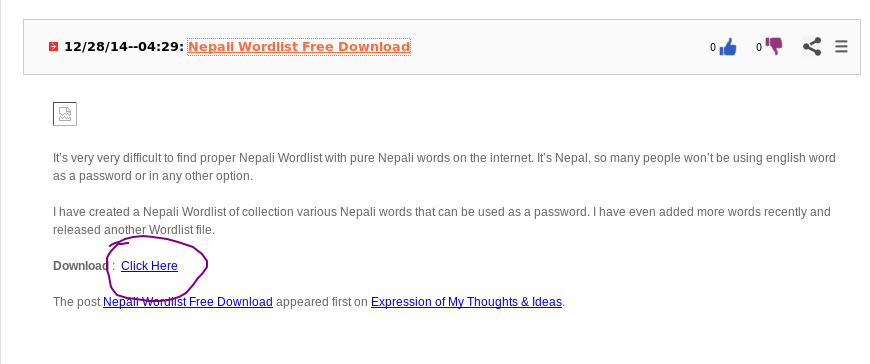
now lets click here and Download the word list, clicking on the link sends you to
http://www.mediafire.com/file/q38m0a0ht3mfc9h/Nepali_Wordlist.zip/file
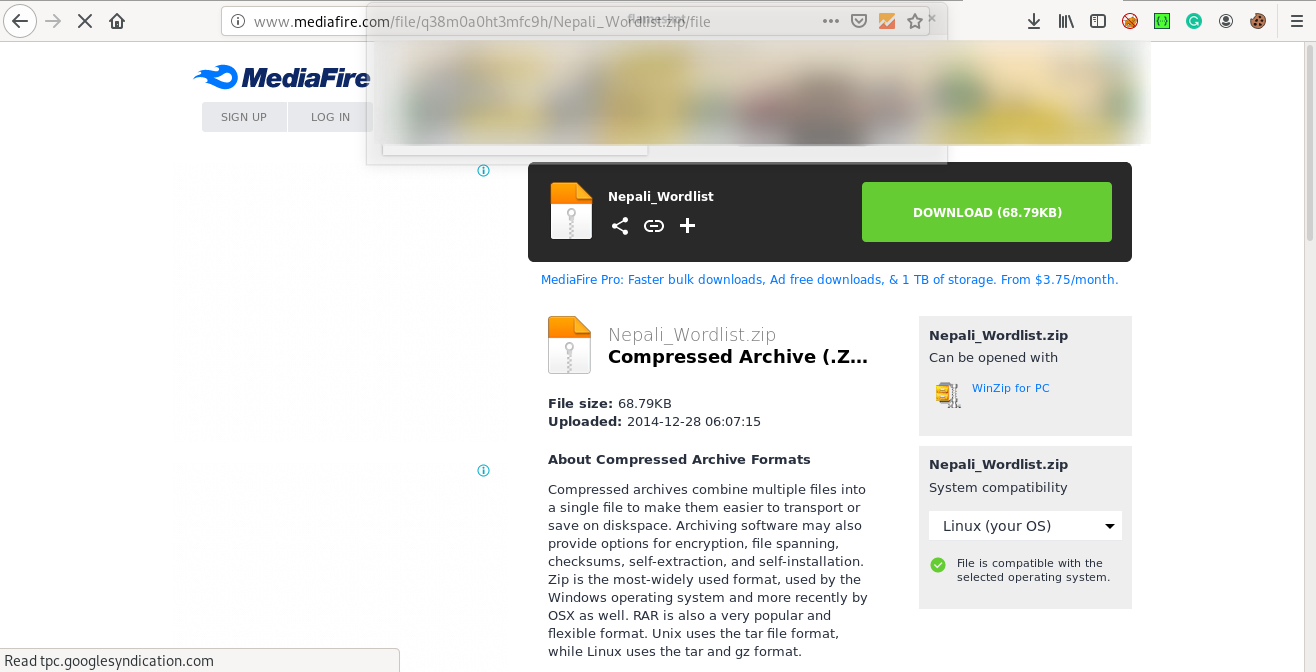
Now lets download the wordlist :)
now open your Burp Suite
lets intercept a random password on burp
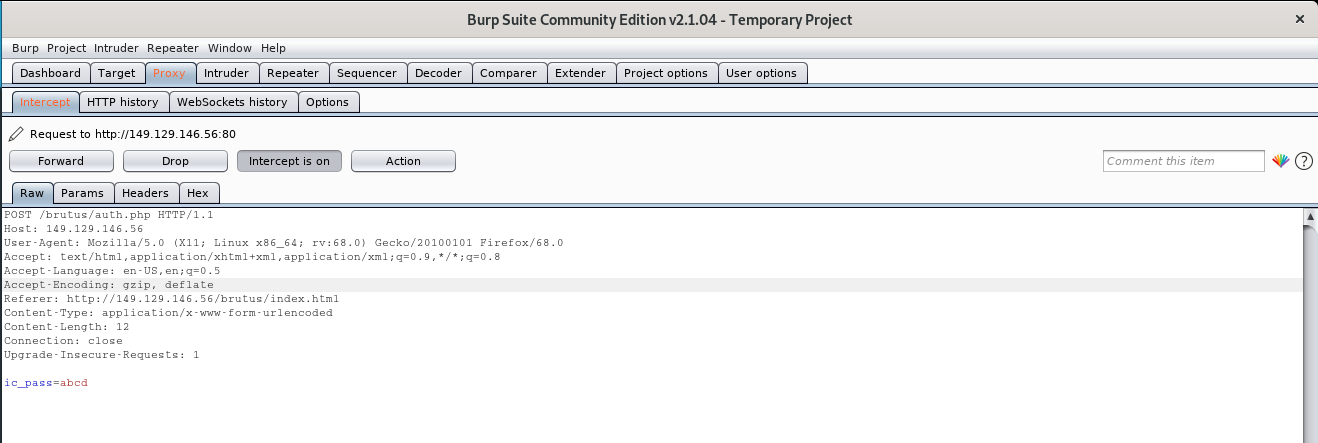
let move it to intruder
the shortcut keys are
ctrl+i to send to intruder and ctrl+shift+i to change the tab
lets set the payload to ic_pass which default the intruder sets to
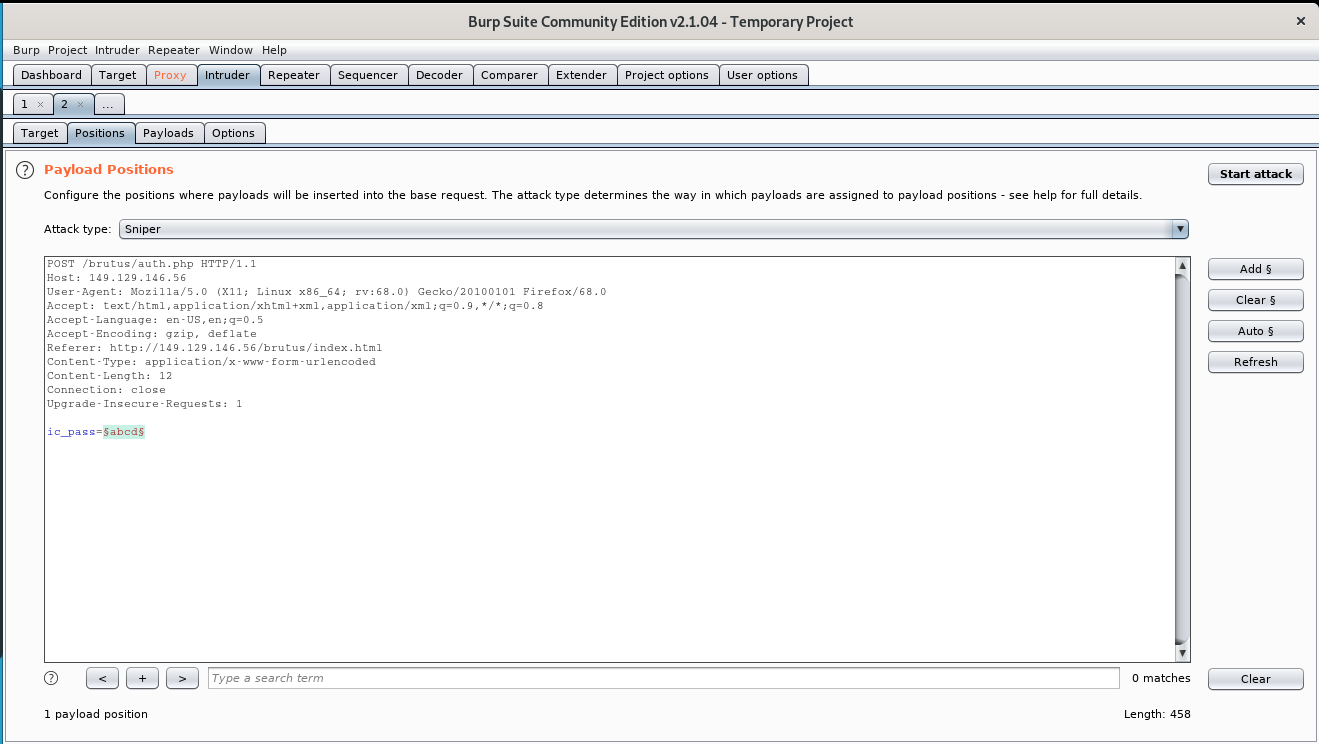
now lets change the tab to pay load and copy and paste the nepali wordlist
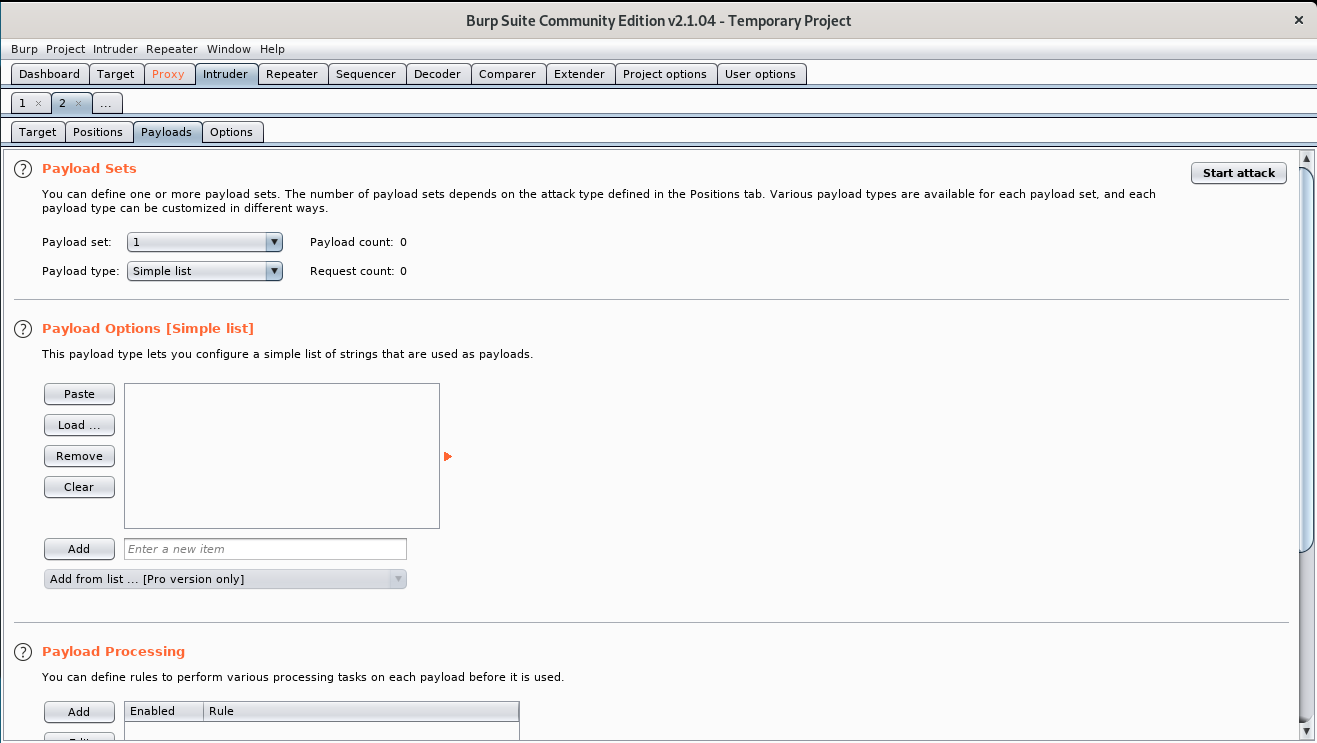
if you have a burp pro you can directly add from list XD
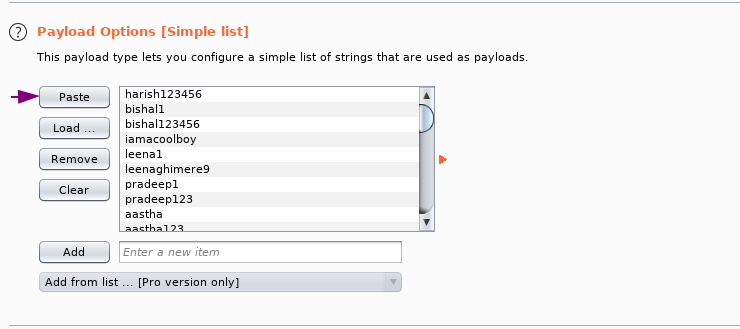
lets start the attack
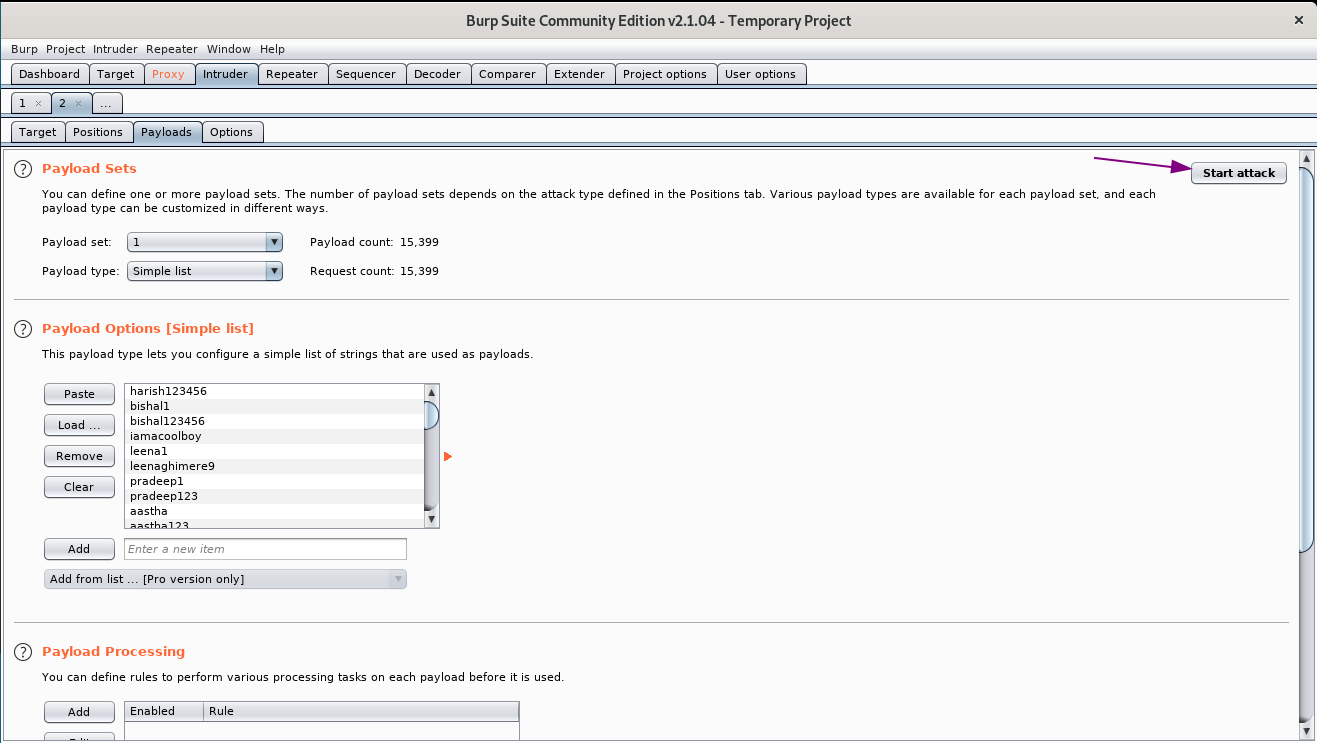
lets wait until the attack ends
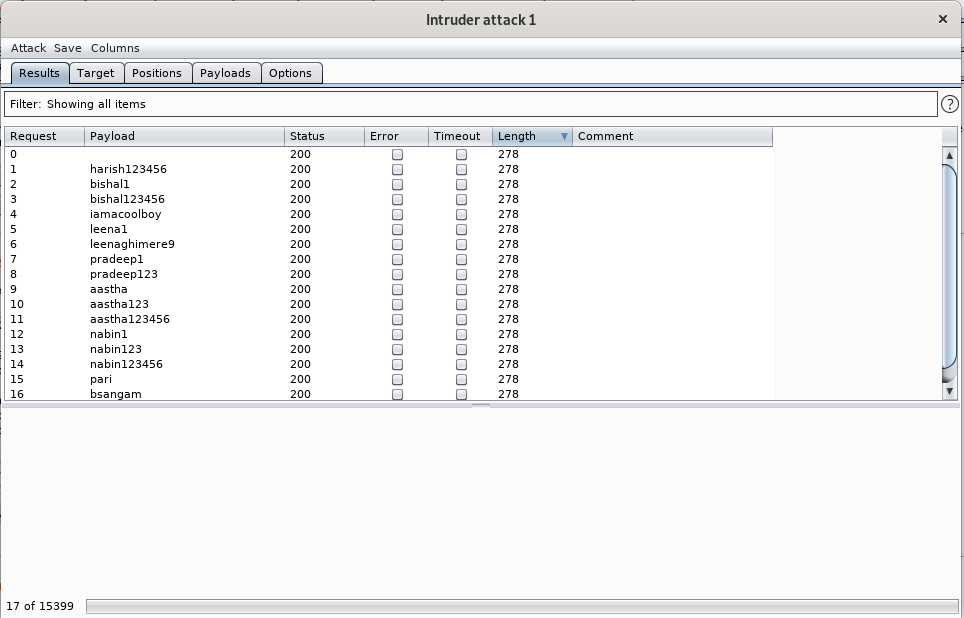
Now wait for the right password to come in and then enter your password and you get the flag :)


